
Syllabus UNIT 1: Introduction to Cybercrime UNIT 2:Cyber offenses UNIT 3: Cybercrime: Mobile and Wireless devices UNIT 4: Tools and method used in Cybercrime. - ppt download

Hacking is Magic - Hack Email using Web Jacking Method | Hacking Is Magic ▭▭▻http://hackingismagic.blogspot.in/ ▭▭▻https://www.facebook.com/hackingismagic This is most commonly used in phishing attacks today -craft an e-mail, or create a fake





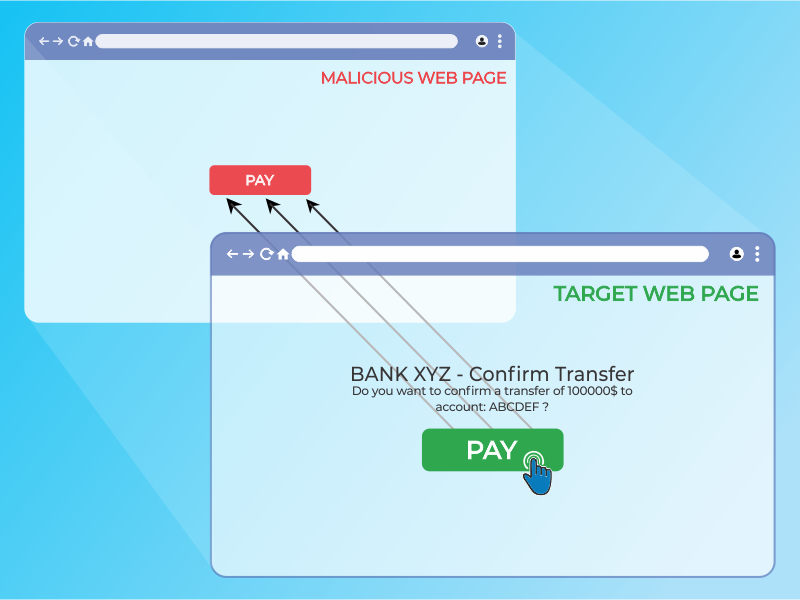










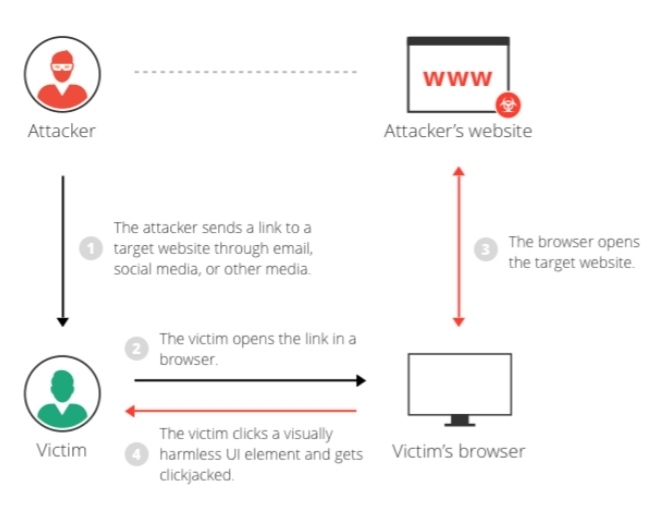
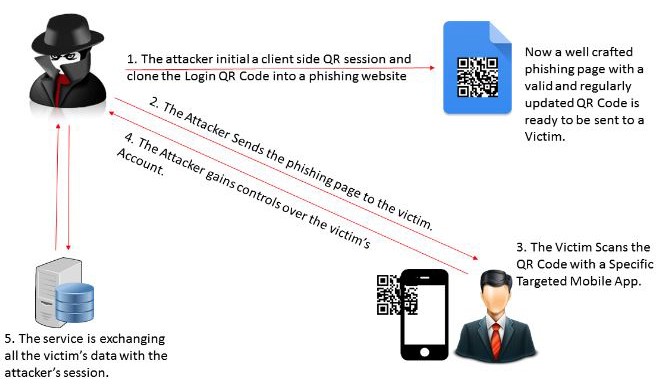

![Cyber Jacking [Quicklist of Cyber Jacking Attack Types]| CYBERPUNK Cyber Jacking [Quicklist of Cyber Jacking Attack Types]| CYBERPUNK](https://cdn.cyberpunk.rs/wp-content/uploads/2019/06/cyberjacking_bg.jpg)





