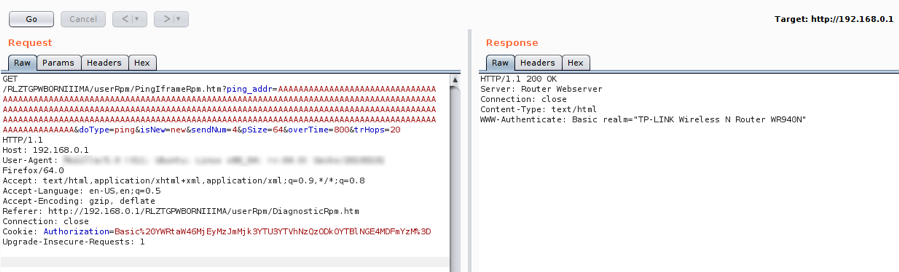
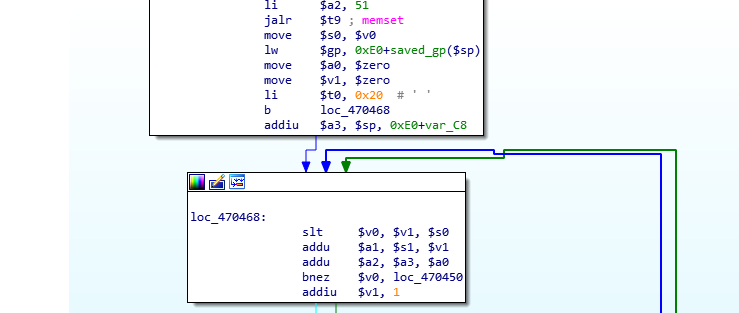
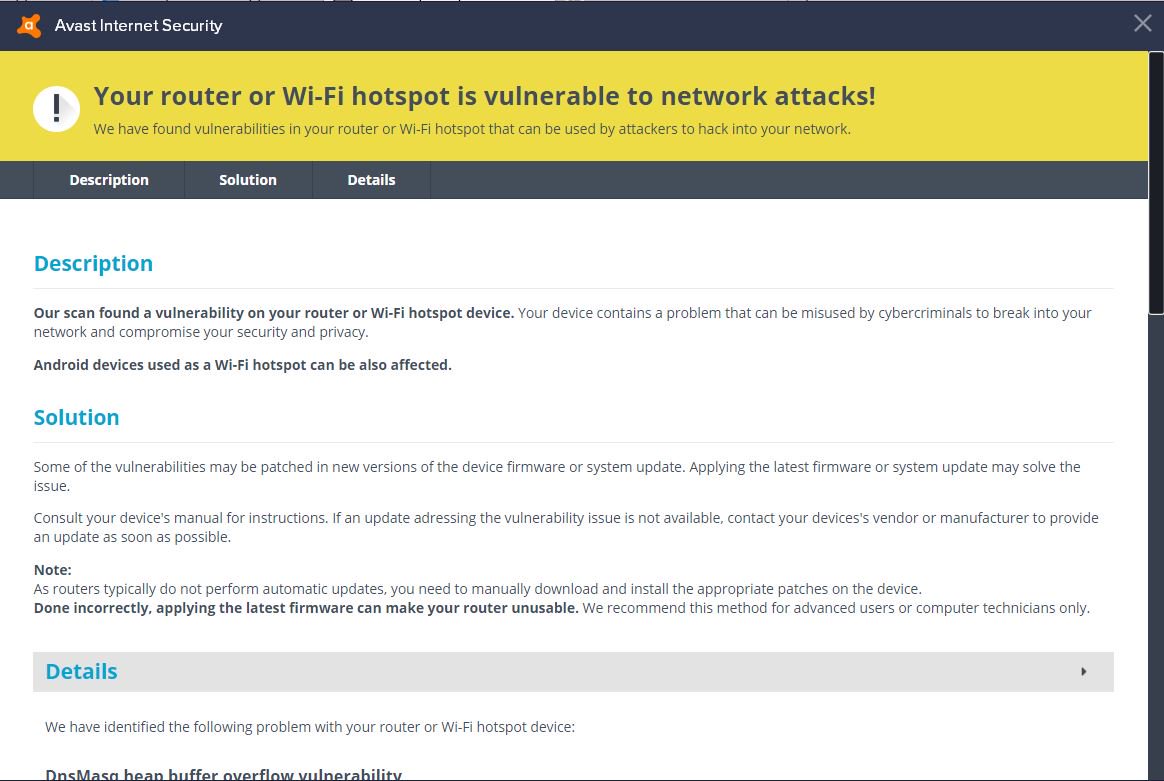
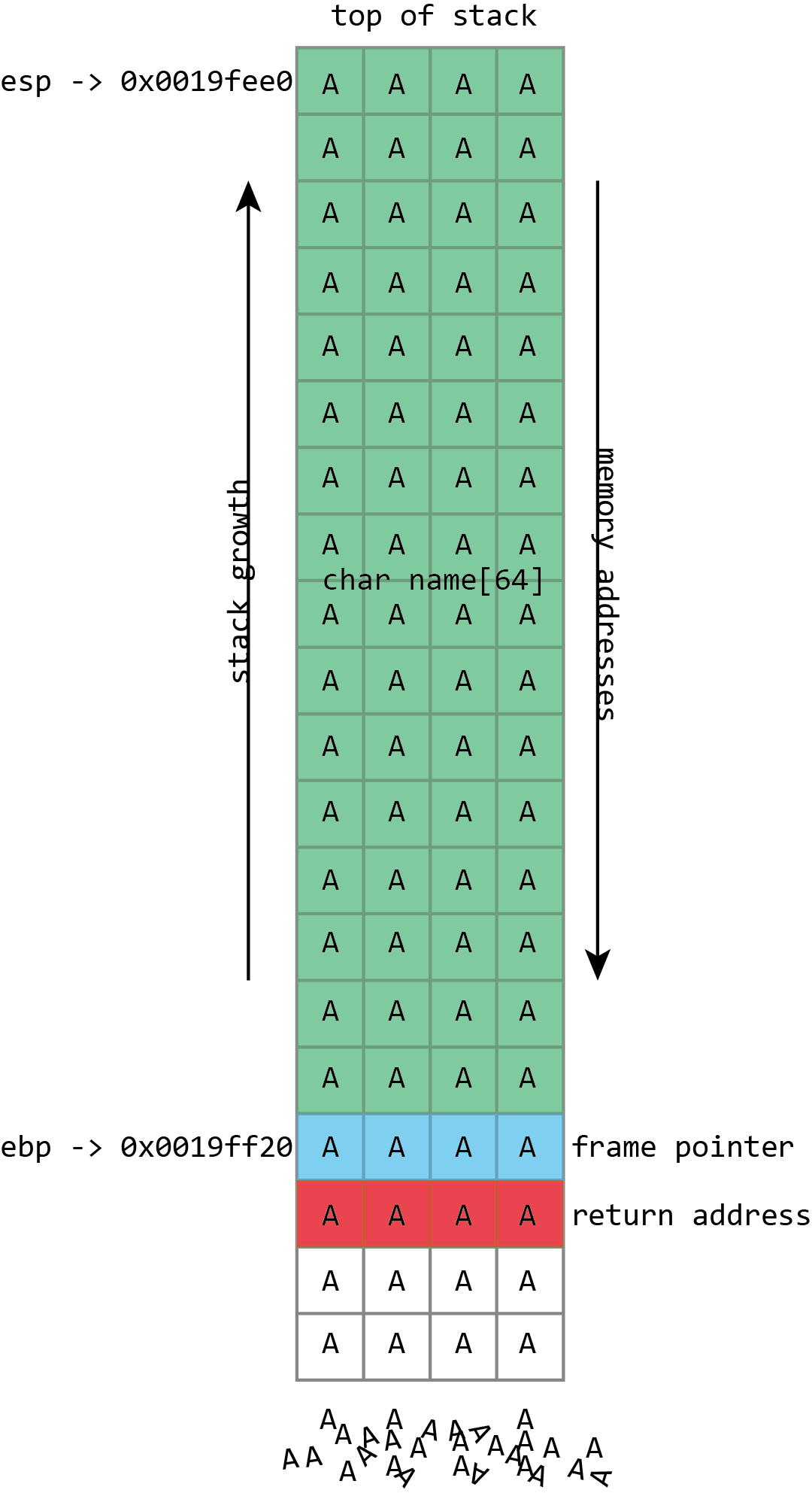
How To Fix CVE-2021-45608- A RCE Vulnerability In NetUSB Affect Millions Of Routers? - The Sec Master
Exploitation of a Vanilla Buffer Overflow in the o2 HomeBox 6441 Router (unauthenticated) - A Step by Step Abuse Guide - NSIDE ATTACK LOGIC GmbH

How To Fix CVE-2021-34991- A Pre-Authentication Buffer Overflow On Multiple Netgear Products? - The Sec Master
![TP-Link TL-WR840N devices allow remote attackers to cause a denial of service (networking outage) via fragmented packets – Buffer Overflow [CVE-2018-15840]: – HackingVila TP-Link TL-WR840N devices allow remote attackers to cause a denial of service (networking outage) via fragmented packets – Buffer Overflow [CVE-2018-15840]: – HackingVila](https://hackingvila.files.wordpress.com/2019/02/main.jpg)
TP-Link TL-WR840N devices allow remote attackers to cause a denial of service (networking outage) via fragmented packets – Buffer Overflow [CVE-2018-15840]: – HackingVila
![ExpressVPN Router] Integer Buffer Overflow: Server Info Disclosure When Router's Nginx Server used as Reverse Proxy Server - CrowdStream - Bugcrowd ExpressVPN Router] Integer Buffer Overflow: Server Info Disclosure When Router's Nginx Server used as Reverse Proxy Server - CrowdStream - Bugcrowd](https://logos.bugcrowdusercontent.com/logos/1b1e/7e4f/8a83d449/6f5d19129ca13d3c5537b6d78687d8f4_ExpressVPN_Monogram_Logo_White__1_.png)
ExpressVPN Router] Integer Buffer Overflow: Server Info Disclosure When Router's Nginx Server used as Reverse Proxy Server - CrowdStream - Bugcrowd
![TP-Link Wireless N Router WR840N – ARP Poisoning cause Buffer Overflow / Upgraded-ARP-Poisoning tool [CVE-2021-29280] : – HackingVila TP-Link Wireless N Router WR840N – ARP Poisoning cause Buffer Overflow / Upgraded-ARP-Poisoning tool [CVE-2021-29280] : – HackingVila](https://hackingvila.files.wordpress.com/2021/04/arp_cache_poisoning.jpg?w=1024)