
Remotely Triggered Black Hole Filtering in IP Version 6 for Cisco IOS, Cisco IOS XE, and Cisco IOS XR Software

How to configure Remotely Triggered Black Hole routing to protect from DDOS attacks (with bonus) - RouterFreak
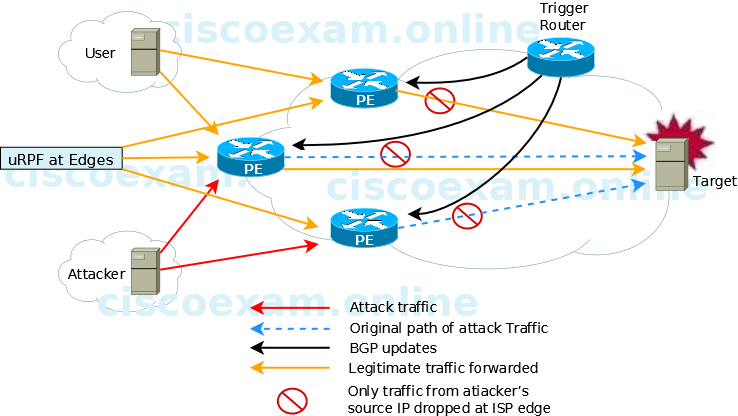
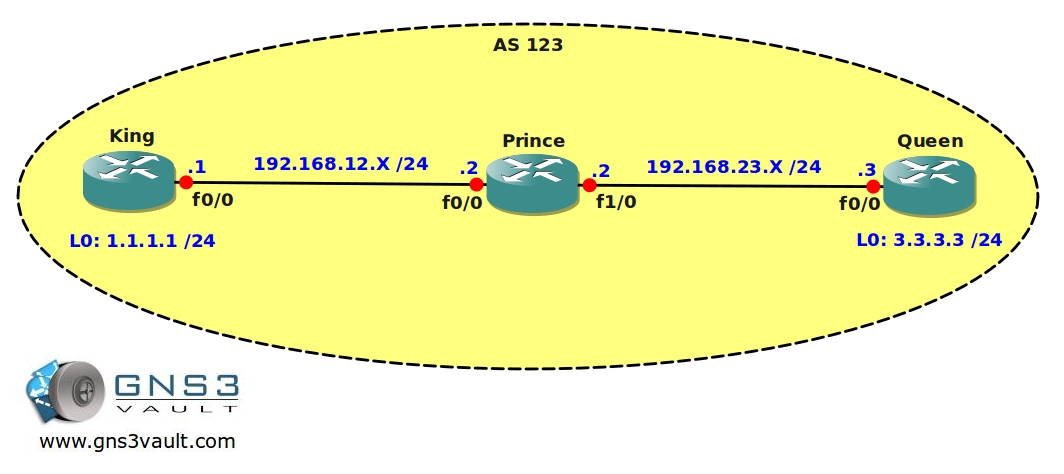
When implementing source-based remote-triggered black hole filtering, which two configurations are required on the edge routers that are not the signaling router?

Mitigation of black hole attacks in Routing Protocol for Low Power and Lossy Networks - Ahmed - 2016 - Security and Communication Networks - Wiley Online Library

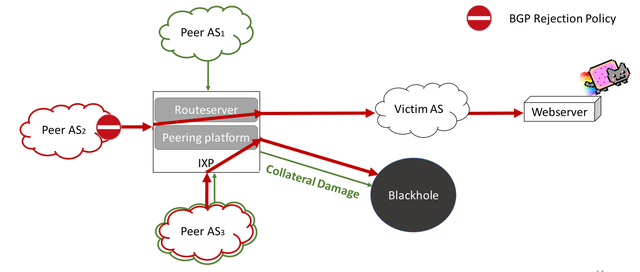
Configure Remotely Triggered Black Hole (RTBH) using Blackhole Community to mitigate DDoS – Awal's Tech Blog
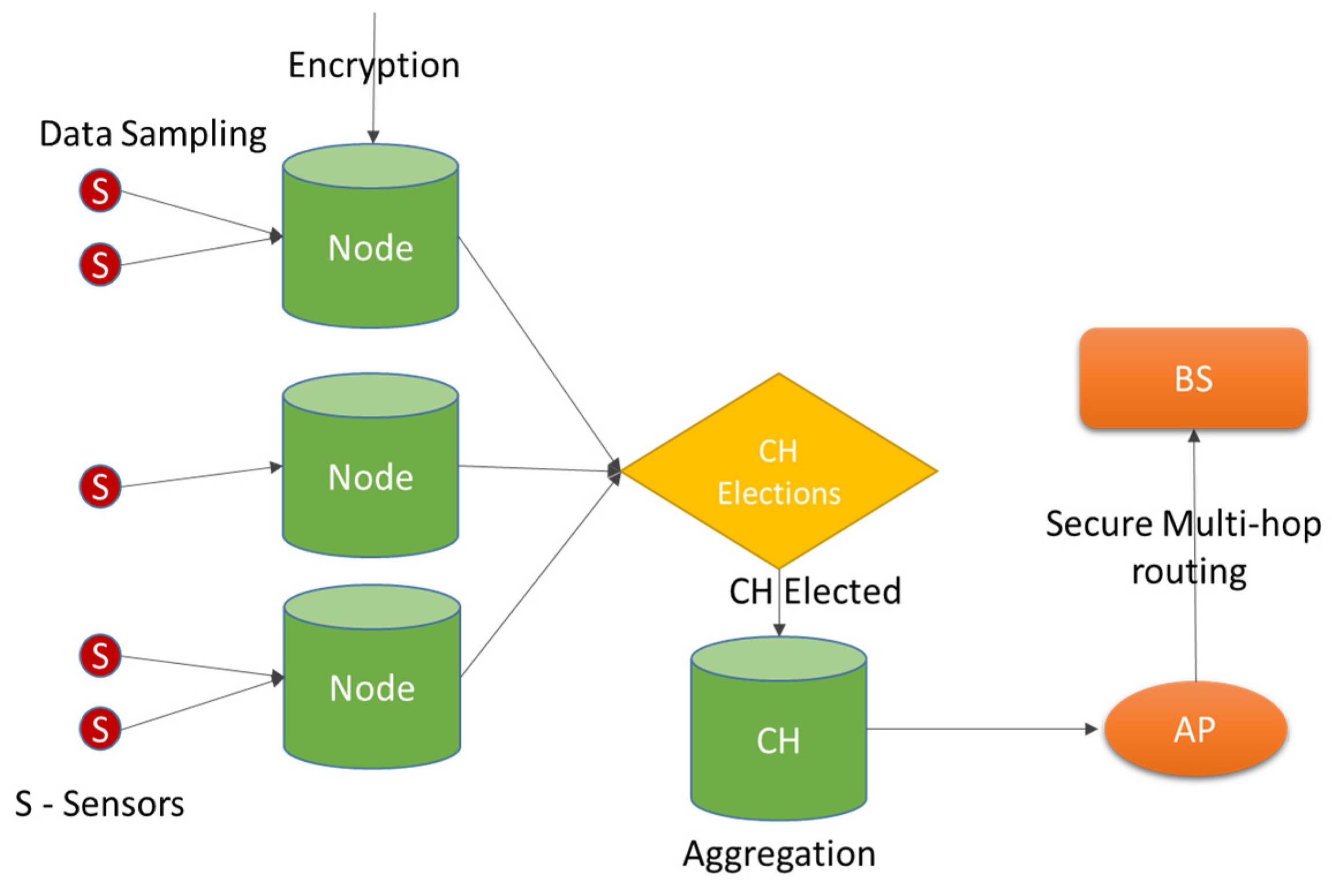
Sensors | Free Full-Text | Defence against Black Hole and Selective Forwarding Attacks for Medical WSNs in the IoT
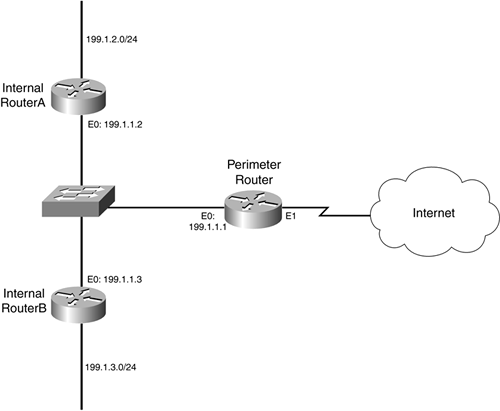

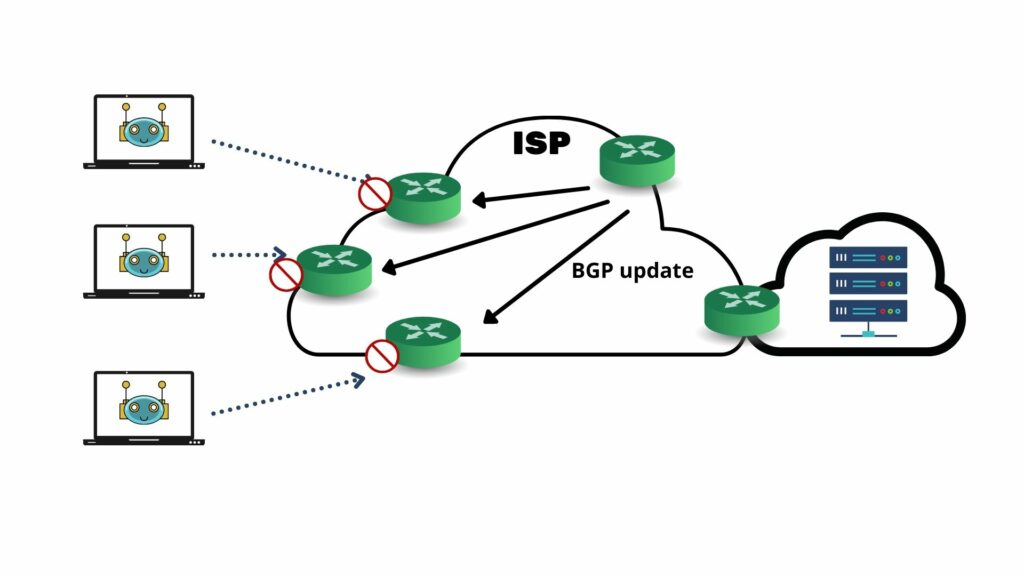




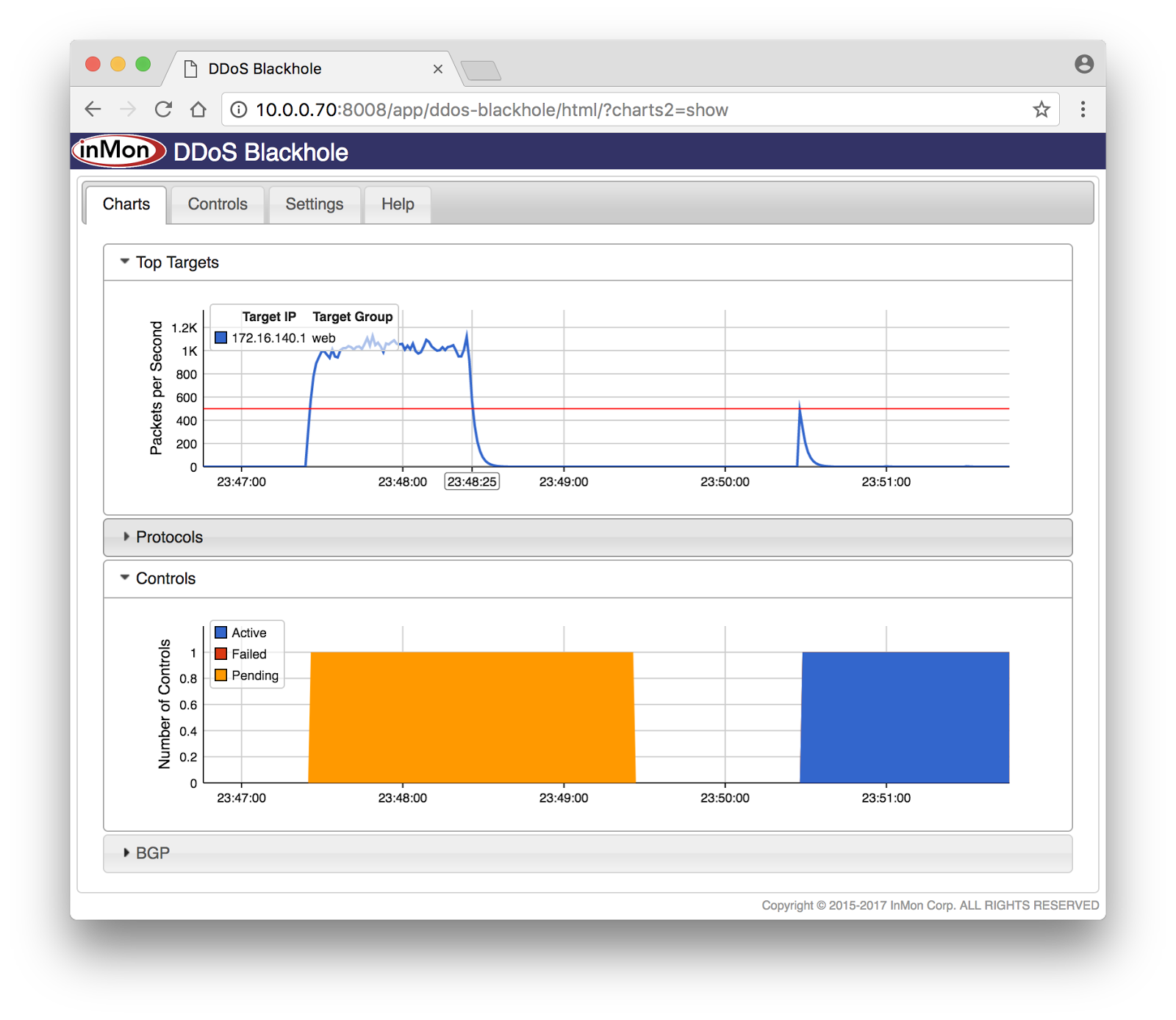

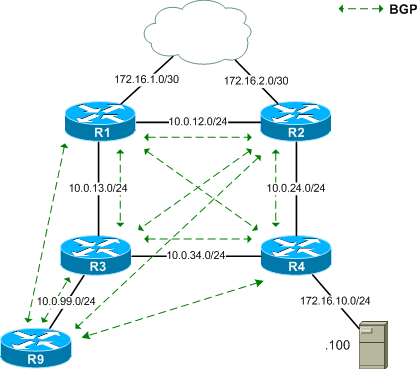

![How to Use BlackHole on M1 Macs [Tutorial] - AVTouchBar How to Use BlackHole on M1 Macs [Tutorial] - AVTouchBar](https://www.avtouchbar.com/wp-content/uploads/2021/09/Audio-Midi-Header-Image.png)
